Difference between revisions of "Netgear WN3000RP"
0x00string (talk | contribs) (Created page with "__FORCETOC__ {{Disclaimer}} thumb|320px Category:Netgear WN3000RP =Netgear WN3000RP= The Netgear WN3000RP is a wifi range extender which ru...") |
|||
| (4 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
__FORCETOC__ | __FORCETOC__ | ||
{{Disclaimer}} | {{Disclaimer}} | ||
[[File:NETGEAR_WN3000RP.JPG|thumb | [[File:NETGEAR_WN3000RP.JPG|120px|left|thumb]] | ||
[[Category: | [[Category:Networking]] | ||
=Netgear WN3000RP= | =Netgear WN3000RP= | ||
| Line 10: | Line 10: | ||
"Move around with your mobile devices and keep them connected by giving your existing WiFi coverage a boost. This small, easy-to-install wall-plug WiFi range extender also creates new WiFi connectivity for up to 1 wired device like a Smart TV, Blu-ray player or game console." | "Move around with your mobile devices and keep them connected by giving your existing WiFi coverage a boost. This small, easy-to-install wall-plug WiFi range extender also creates new WiFi connectivity for up to 1 wired device like a Smart TV, Blu-ray player or game console." | ||
[https://www.amazon.com/NETGEAR-Version-Wi-Fi-Extender-WN3000RP/dp/B004YAYM06/ Amazon] | == Purchase == | ||
Buying devices is expensive and, in a lot of cases our testing leads to bricked equipment. If you would like to help support our group, site, and research please use one of the links below to purchase your next device. | |||
[https://www.amazon.com/NETGEAR-Version-Wi-Fi-Extender-WN3000RP/dp/B004YAYM06/ref=as_li_ss_tl?ie=UTF8&qid=1501935929&sr=8-1&keywords=Netgear+WN3000RP&linkCode=ll1&tag=exploiteers-20&linkId=5e5aa8977a10c2751bece1a884efefa8 Purchase the Netgear WN3000RP at Amazon] | |||
==Hardware Root== | |||
== | |||
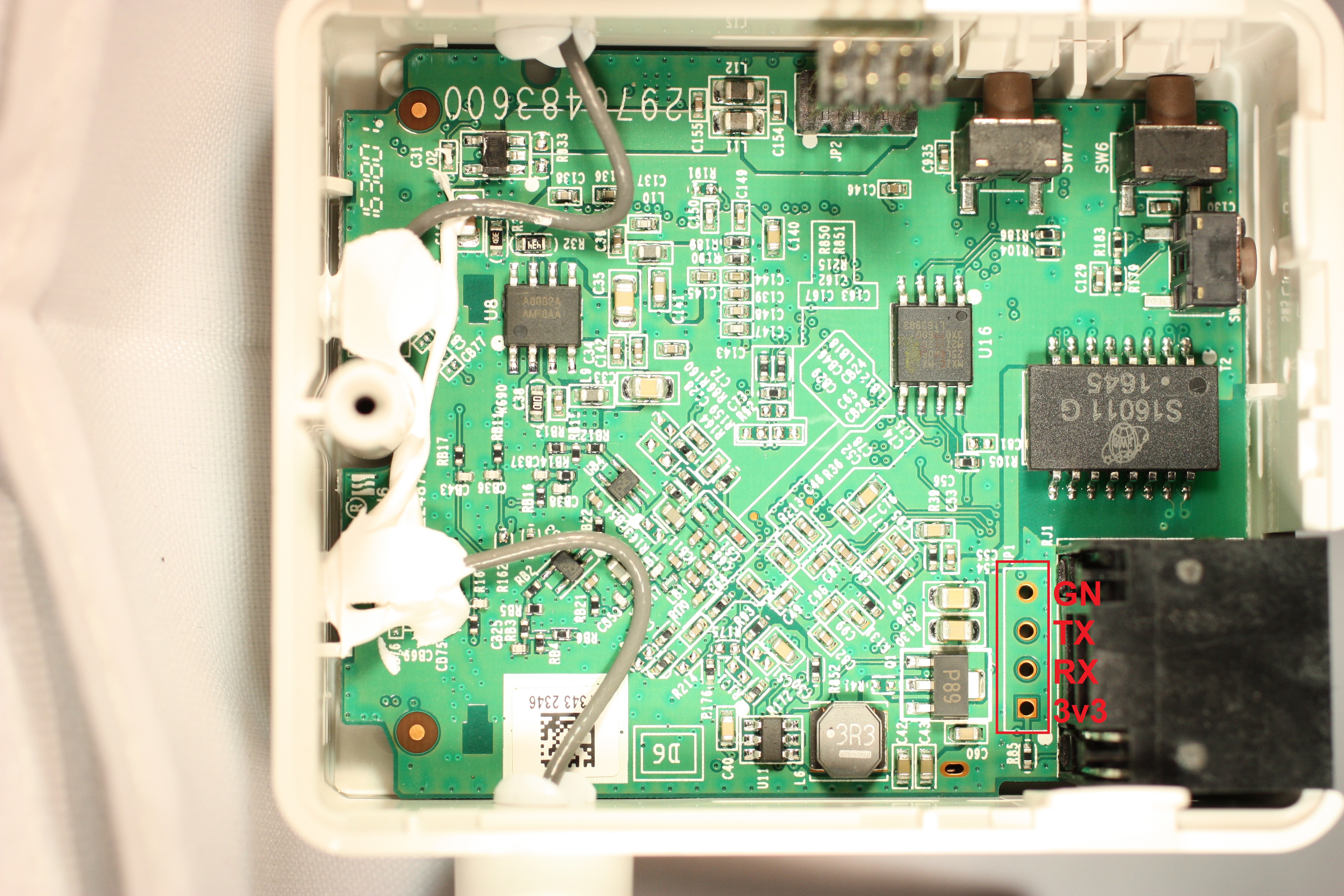
The UART interface on this device is located [pictured], and runs at 57600,8n1. Once the device completes booting, a root shell is executed on the UART TTY. a telnet daemon can be launched by executing '/usr/sbin/telnetd &' | The UART interface on this device is located [pictured], and runs at 57600,8n1. Once the device completes booting, a root shell is executed on the UART TTY. a telnet daemon can be launched by executing '/usr/sbin/telnetd &' | ||
<gallery> | |||
NETGEAR_WN3000RP_UART.JPG | |||
</gallery> | |||
== | ===UART Output=== | ||
<pre> | <pre> | ||
Miniterm.py -p /dev/ttyUSB0 -b 57600 | Miniterm.py -p /dev/ttyUSB0 -b 57600 | ||
Latest revision as of 12:27, 5 August 2017
"Although the information we release has been verified and shown to work to the best our knowledge, we cant be held accountable for bricked devices or roots gone wrong."
Netgear WN3000RP
The Netgear WN3000RP is a wifi range extender which runs OpenWRT KAMIKAZE on MIPS32.
"Move around with your mobile devices and keep them connected by giving your existing WiFi coverage a boost. This small, easy-to-install wall-plug WiFi range extender also creates new WiFi connectivity for up to 1 wired device like a Smart TV, Blu-ray player or game console."
Purchase
Buying devices is expensive and, in a lot of cases our testing leads to bricked equipment. If you would like to help support our group, site, and research please use one of the links below to purchase your next device. Purchase the Netgear WN3000RP at Amazon
Hardware Root
The UART interface on this device is located [pictured], and runs at 57600,8n1. Once the device completes booting, a root shell is executed on the UART TTY. a telnet daemon can be launched by executing '/usr/sbin/telnetd &'
UART Output
Miniterm.py -p /dev/ttyUSB0 -b 57600
_______ ________ __
| |.-----.-----.-----.| | | |.----.| |_
| - || _ | -__| || | | || _|| _|
|_______|| __|_____|__|__||________||__| |____|
|__| W I R E L E S S F R E E D O M
KAMIKAZE (bleeding edge, r18571) ------------------
* 10 oz Vodka Shake well with ice and strain
* 10 oz Triple sec mixture into 10 shot glasses.
* 10 oz lime juice Salute!
---------------------------------------------------
root@WN3000RPv3:/# /usr/sbin/telnetd &