Difference between revisions of "FireFU Exploit"
| (2 intermediate revisions by the same user not shown) | |||
| Line 47: | Line 47: | ||
# AFTV Cube (stark) or Pendant (needle) | # AFTV Cube (stark) or Pendant (needle) | ||
# HDMI breakout or an HDMI cable that can be cut | # HDMI breakout or an HDMI cable that can be cut | ||
#* [https://www.amazon.com/ | #* [https://www.amazon.com/Uniquers-Panel-Socket-Terminal-Breakout/dp/B071X4GX2B/ref=as_li_ss_tl?ie=UTF8&qid=1542181679&sr=8-6&keywords=hdmi+breakout&dpID=41jAiKXfLKL&preST=_SX300_QL70_&dpSrc=srch&linkCode=ll1&tag=exploiteers-20&linkId=3c2f3339c59aefd8559323021283ef92&language=en_US HDMI Breakout on Amazon (Affiliate Link)] | ||
# Arduino, Teensy or any Arduino compatible dev board that provides an I2C bus. | # Arduino, Teensy or any Arduino compatible dev board that provides an I2C bus. | ||
#* [https://www.amazon.com/Arduino-Org-A000062-Due/dp/B00A6C3JN2/ref=as_li_ss_tl?ie=UTF8&qid=1541056875&sr=8-3&keywords=arduino+due&linkCode=ll1&tag=exploiteers-20&linkId=c6276ccad04129d9264a77595484c157 Arduino Due on Amazon (Affiliate Link)] | #* [https://www.amazon.com/Arduino-Org-A000062-Due/dp/B00A6C3JN2/ref=as_li_ss_tl?ie=UTF8&qid=1541056875&sr=8-3&keywords=arduino+due&linkCode=ll1&tag=exploiteers-20&linkId=c6276ccad04129d9264a77595484c157 Arduino Due on Amazon (Affiliate Link)] | ||
| Line 58: | Line 58: | ||
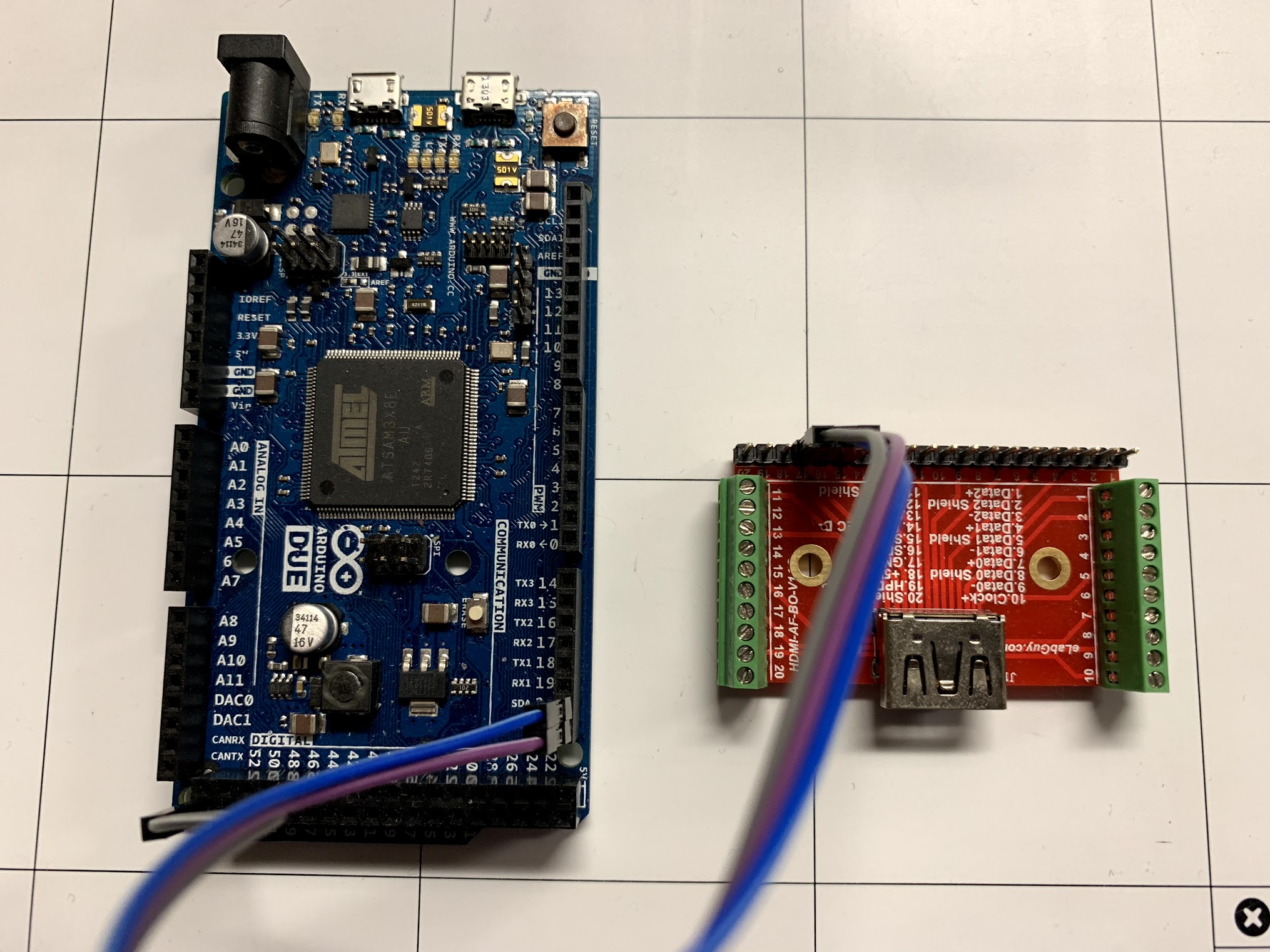
#connect following pin to your Arduino <table><tr><th>HDMI</th><th>Arduino</th></tr><tr><td>PIN 15 (SCL)</td><td>I2C SCL</td></tr><tr><td>PIN 16 (SDA)</td><td>I2C SDA</td></tr><tr><td>PIN 17 (GND)</td><td>I2C GND</td></tr></table> | #connect following pin to your Arduino <table><tr><th>HDMI</th><th>Arduino</th></tr><tr><td>PIN 15 (SCL)</td><td>I2C SCL</td></tr><tr><td>PIN 16 (SDA)</td><td>I2C SDA</td></tr><tr><td>PIN 17 (GND)</td><td>I2C GND</td></tr></table> | ||
#Hook up the Arduino to your PC and flash the hdmi_arduino.ino sketch in the hdmi_dongle/hdmi_arduino folder. | #Hook up the Arduino to your PC and flash the hdmi_arduino.ino sketch in the hdmi_dongle/hdmi_arduino folder. | ||
[[File:ArduinoHDMII2C.jpg|400px]] | |||
=== Rooting Proccess === | === Rooting Proccess === | ||
Latest revision as of 07:50, 14 November 2018
FireFU
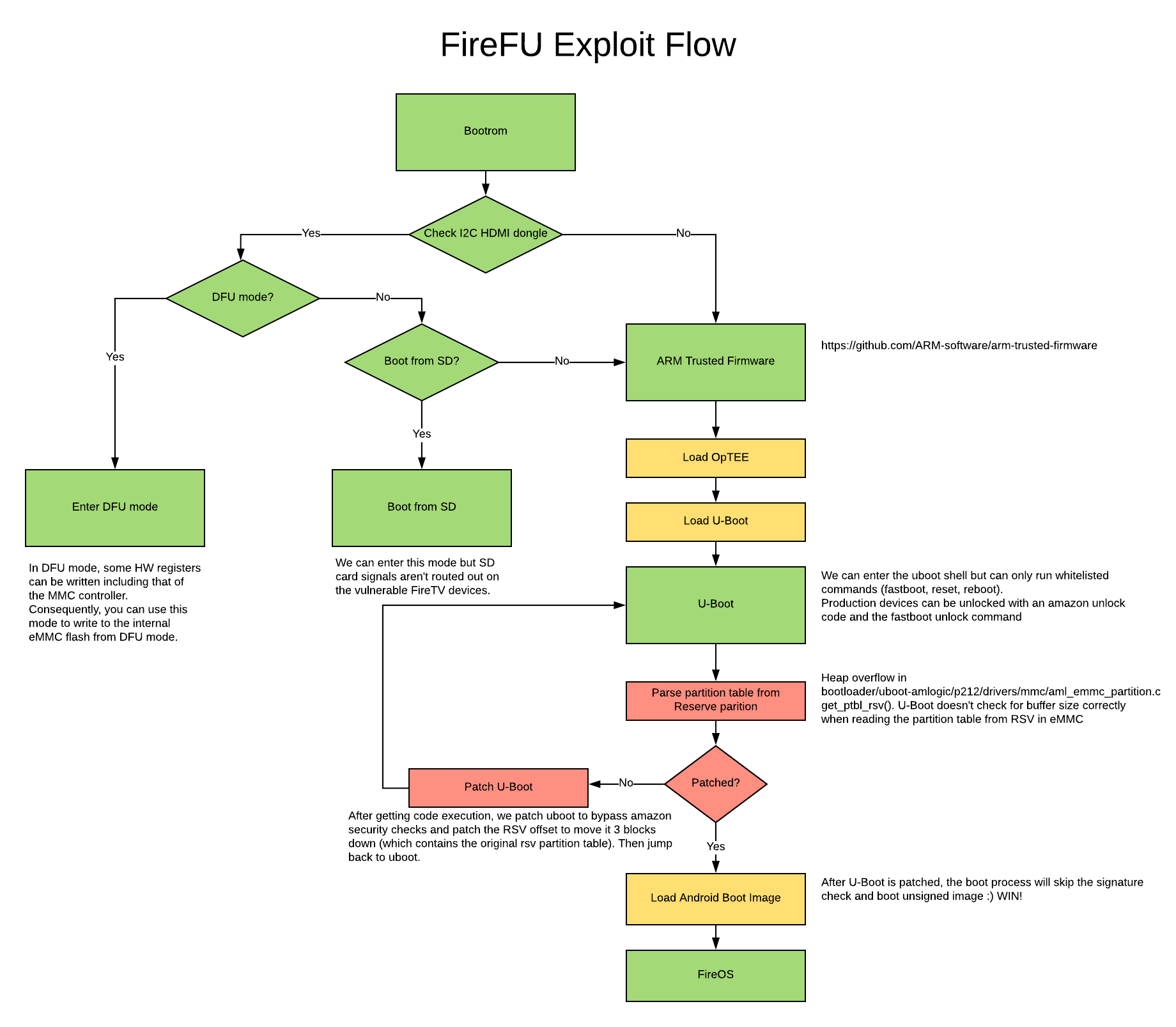
FireFU is an exploit chain leveraging a read write primitive from the FireTV Cube and Pendant’s Amlogic S905Z microcontroller along with a heap overflow within the parsing of the devices RSV partition table allowing for the running of unsigned code.
Attack Summary
This is all done through the exploit's install script but is documented here for the curious.
- We enter DFU mode by connecting to the devices HDMI port and passing “boot@USB” to the Amlogic S905Z through the HDMI’s i2c interface.
- In DFU mode, we are able to read and write memory. we leverage the read/write primitive to write to hardware registers for the MMC controller.
- After entering DFU, we write to the emmc controller to modify the devices flash.
- We copy the original RSV table to a new locations 3 blocks away.
- We modify the partition table layout to exploit a heap overflow within u-boot
- Heap overflow can be found in “bootloader/uboot-amlogic/p212/drivers/mmc/aml_emmc_partition.c” - get_ptbl_rsv()
- U-Boot doesn't check for buffer size correctly when reading the partition table from RSV in eMMC
- Exploit modifies the following in RAM
- amzn_target_is_unlocked() to alway return 1
- patch amzn_dm_verity_is_off to return true
- patch amzn_target_device_type to alway return engineering device
- fixup bootm address for fastboot
- Heap overflow can be found in “bootloader/uboot-amlogic/p212/drivers/mmc/aml_emmc_partition.c” - get_ptbl_rsv()
- Because we exploit u-boot early on in the boot chain and we do it every boot, we are able to modify u-boot in ram breaking the secure boot “chain of trust” and allowing for unsigned code to be ran.
- The HDMI i2c connection is then disconnected and the device is rebooted into fastboot
- From fastboot we flash the following
- a new boot.img with magisk installed for superuser access
- a new recovery to fix issues with the Fire Tv recovery accessing the old RSV location.
- From fastboot we flash the following
- We then reboot to complete the root process.
Flow Chart
Exploit
DFU + U-Boot Exploit for AFTV Stark + Needle
- Tested on FW 6.2.5.5 for Needle
- Tested on FW 6.2.5.5 for Stark
Disclaimer
Exploitee.rs would like to remind users that any flashing of unofficial firmware or usage of provided tools is done at your own risk and will likely void your device’s warranty.
Preamble
While this process can be done in a virtual machine, a lot of data is backed up and flashed during this process and a VM environment will drastically slow down communication in DFU mode.
Tools Needed
- AFTV Cube (stark) or Pendant (needle)
- HDMI breakout or an HDMI cable that can be cut
- Arduino, Teensy or any Arduino compatible dev board that provides an I2C bus.
- Linux box
Preparing HDMI dongle
This process has only been tested with the Arduino Due and Teensy 3. Other boards are untested!
- Please check Wikipedia for the standard HDMI pinout: https://en.wikipedia.org/wiki/HDMI
- connect following pin to your Arduino
HDMI Arduino PIN 15 (SCL) I2C SCL PIN 16 (SDA) I2C SDA PIN 17 (GND) I2C GND - Hook up the Arduino to your PC and flash the hdmi_arduino.ino sketch in the hdmi_dongle/hdmi_arduino folder.
Rooting Proccess
- setup udev rules (or equivalent) to allow usb access for
- idVendor=1b8e, idProduct=c003 (aml DFU)
- ID 1b8e:c003 Amlogic, Inc.
- idVendor=18d1, idProduct=0d02 (fastboot)
- ID 18d1:0d02 Google Inc. Celkon A88
- idVendor=1b8e, idProduct=c003 (aml DFU)
- DFU tool depends on libusb so make sure libusb is install
- Connect the HDMI dongle to your AFTV & power to your Arduino (or equivalent)
- Connect micro-usb cable to your AFTV
- Power up the FireTV device
- Check lsusb on your linux box to see if the device has entered DFU mode
- look for something similar to this: ID 1b8e:c003 Amlogic, Inc.
- if the device does not show up then try to reset the FireTV and try again
- Run install_exploit.sh on your linux box
- This process can take about 30min-60min
- Remember to keep your backup safe!
- Side load Magisk Manager apk on your AFTV
- Download APK from https://github.com/topjohnwu/Magisk/releases
- adb install magisk.apk
- Done :)
Miscellaneous Information
Disabling OTA
Any update can remove the code signing update or possibly brick the device. We recommend disabling OTA updates with the following.
- Run following commands as root
- pm disable com.amazon.tv.forcedotaupdater
- pm disable com.amazon.device.software.ota
- pm disable com.amazon.device.software.ota.override
You can also block update DNS domain at your router or install a custom recovery to be safe.
OTA Updates & Installing New Images
After each amazon supplied new image or OTA update, you must patch the boot and recovery images again (because of FireFu's RSV relocation).
Steps to patch boot+recovery image if you accidently flash unpatch image / take OTA image:
- Enter DFU mode with the HDMI dongle
- Dump the boot image:
- ./aml_usb_mmc -r -s 0x16800 -c 0x8000 -f backup_boot.img
- Dump the recovery image:
- ./aml_usb_mmc -r -s 0x1F000 -c 0x8000 -f backup_recovery.img
- Patch the boot image:
- cd magisk_patcher
- ./boot_patch.sh backup_boot.img
- Patch the recovery image:
- cd magisk_patcher
- AFTV_ONLY_RSV_TABLE=1 ./boot_patch.sh backup_recovery.img
- Enter Fastboot:
- Enter DFU mode with the HDMI dongle
- check to see if device enumerated with lsusb. if not, reboot and retry
- run ./aml_reboot fastboot
- The device should now be in fastboot mode
- Flash the boot image:
- fastboot flash boot IMAGE.img
- Flash the recovery image:
- fastboot flash recovery IMAGE.img
Video Demo
Downloads
Below is the download information for the exploit.
Exploit package
This download is intended for users who are only seeking the binaries to perform the exploit.
Source Code
This is for the users who are needing to recompile the exploit or are just curious about the process.