Difference between revisions of "Alarm.com ADC-v520IR"
(Created page with "__FORCETOC__ {{Disclaimer}} 100px|left|thumb Category:Cameras This page will be dedicated to a general overview, descriptions, and inform...") |
|||
| (3 intermediate revisions by the same user not shown) | |||
| Line 4: | Line 4: | ||
[[Category:Cameras]] | [[Category:Cameras]] | ||
This page will be dedicated to a general overview, descriptions, and information related to the Alarm.com ADC-v520IR. | This page will be dedicated to a general overview, descriptions, and information related to the Alarm.com ADC-v520IR. | ||
== About == | |||
The Alarm.com ADC-v520IR is a network (Wifi/Ethernet) camera w/ IR LEDs provided by alarm.com | |||
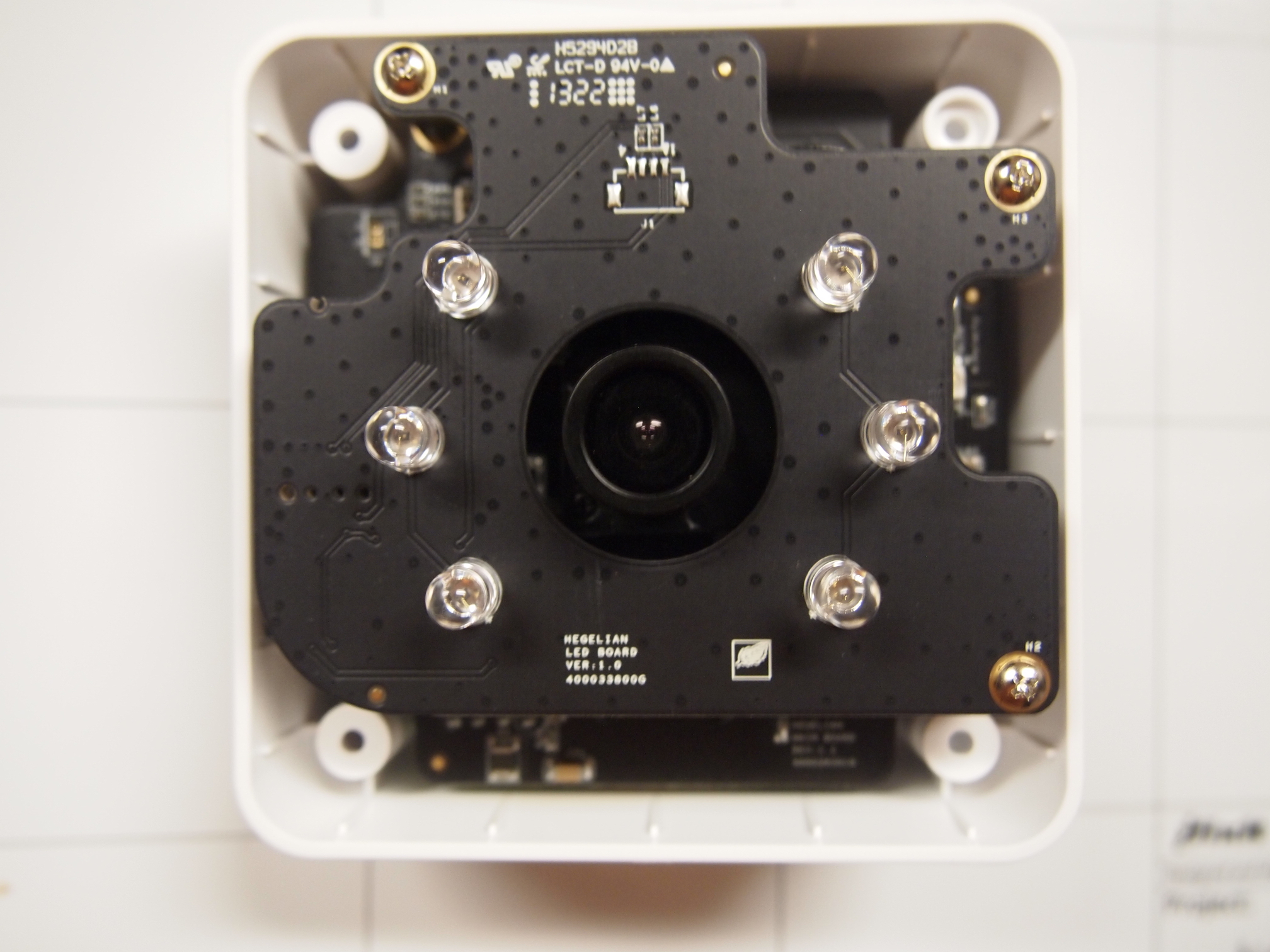
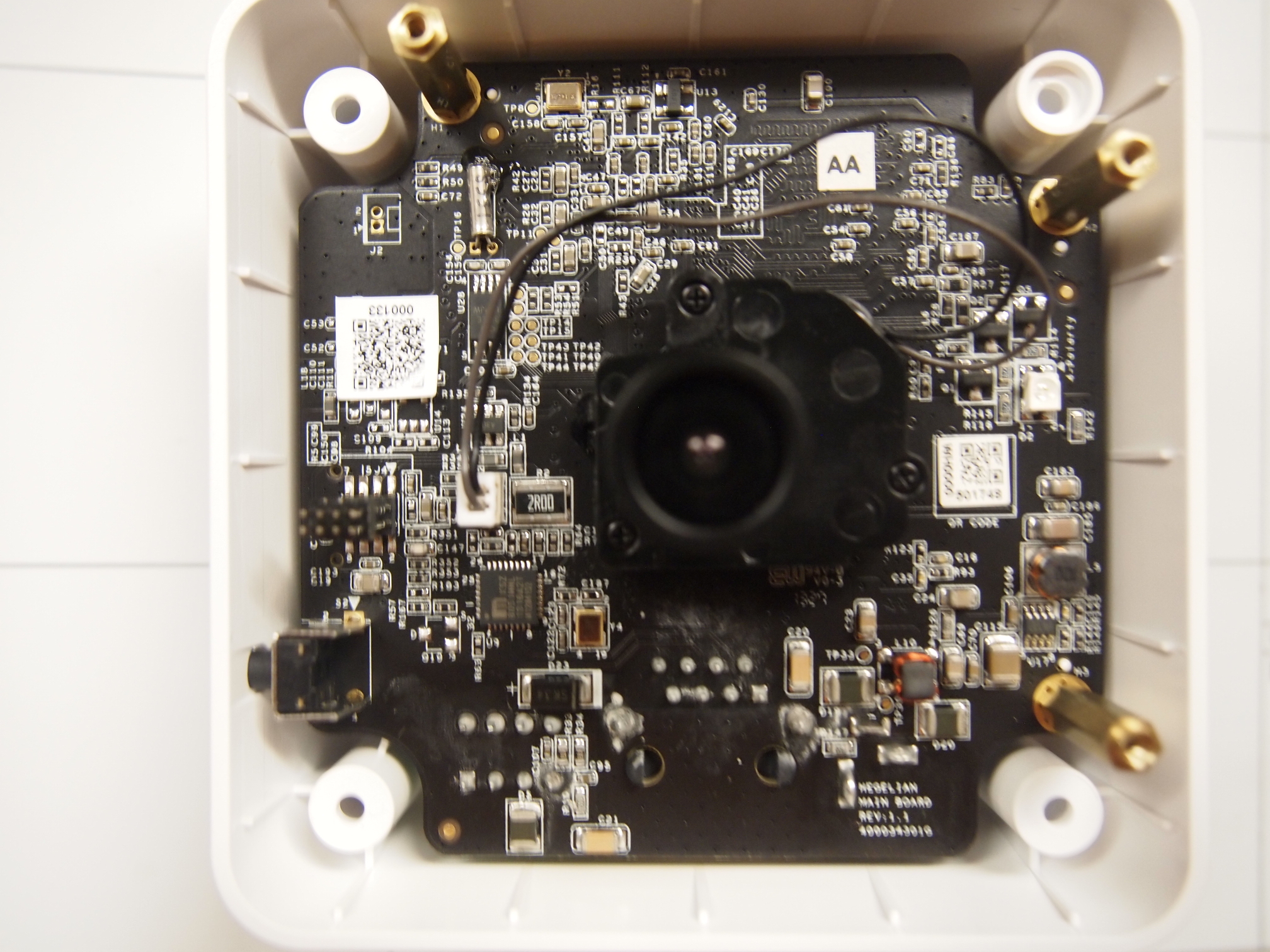
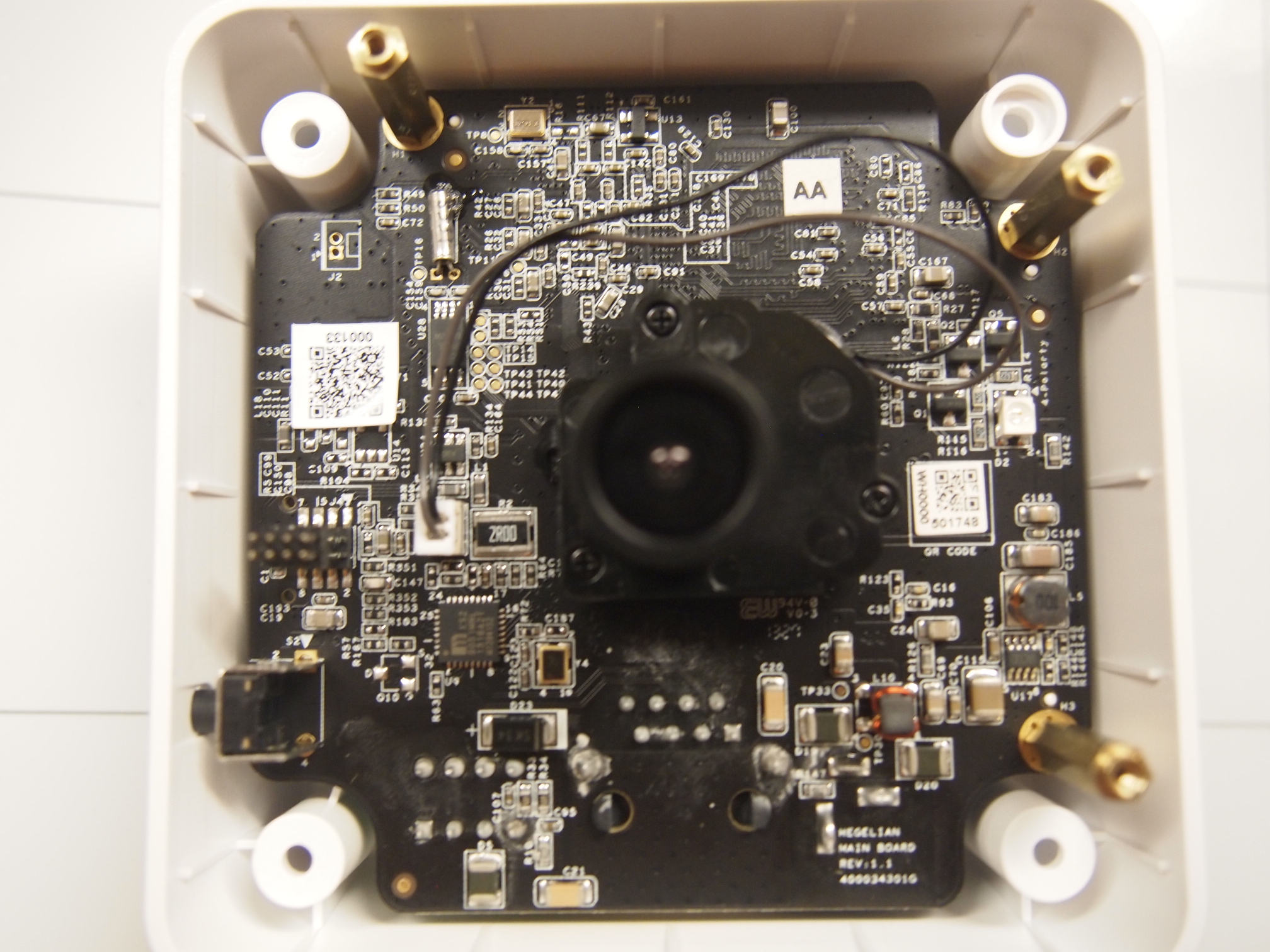
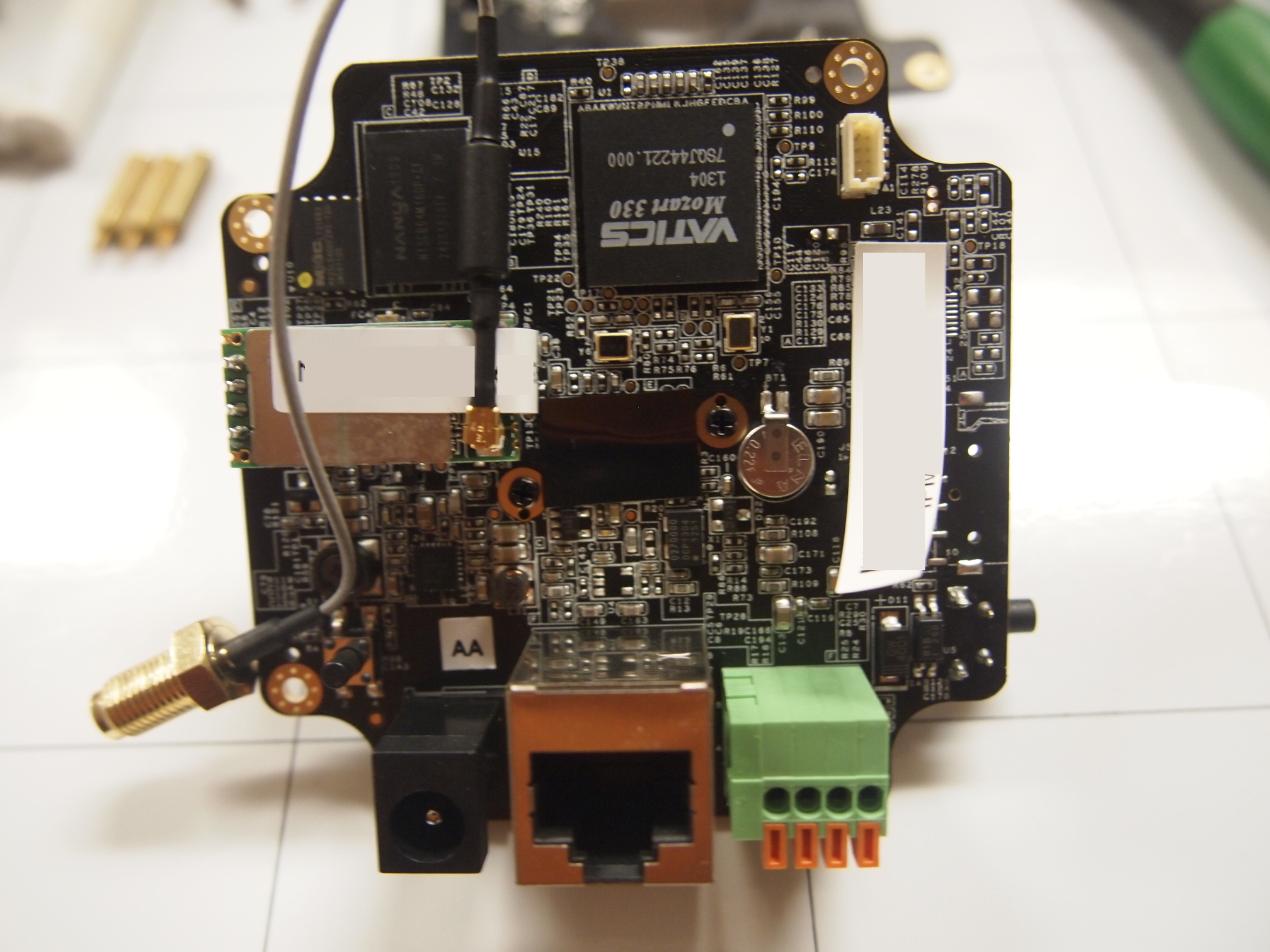
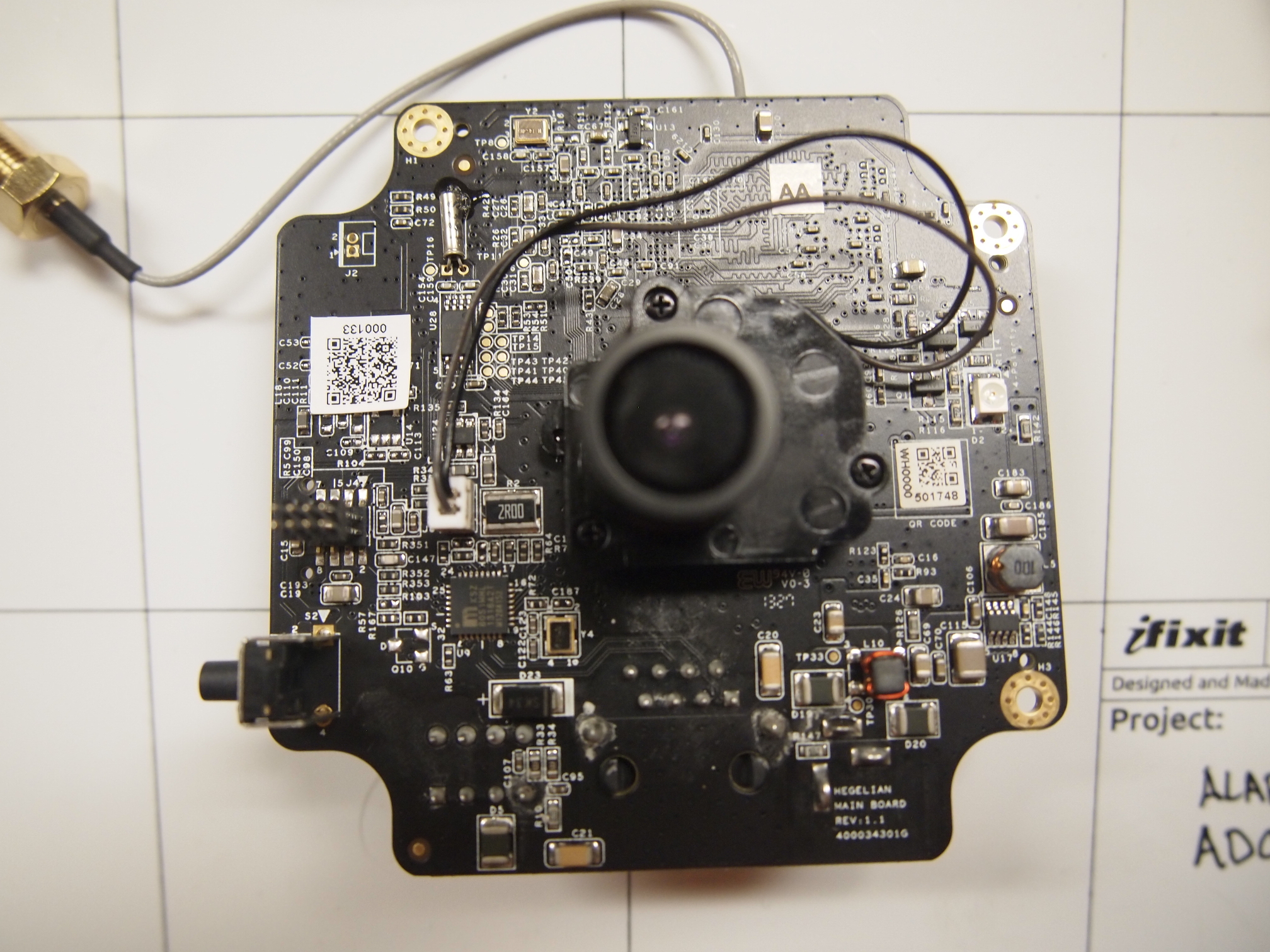
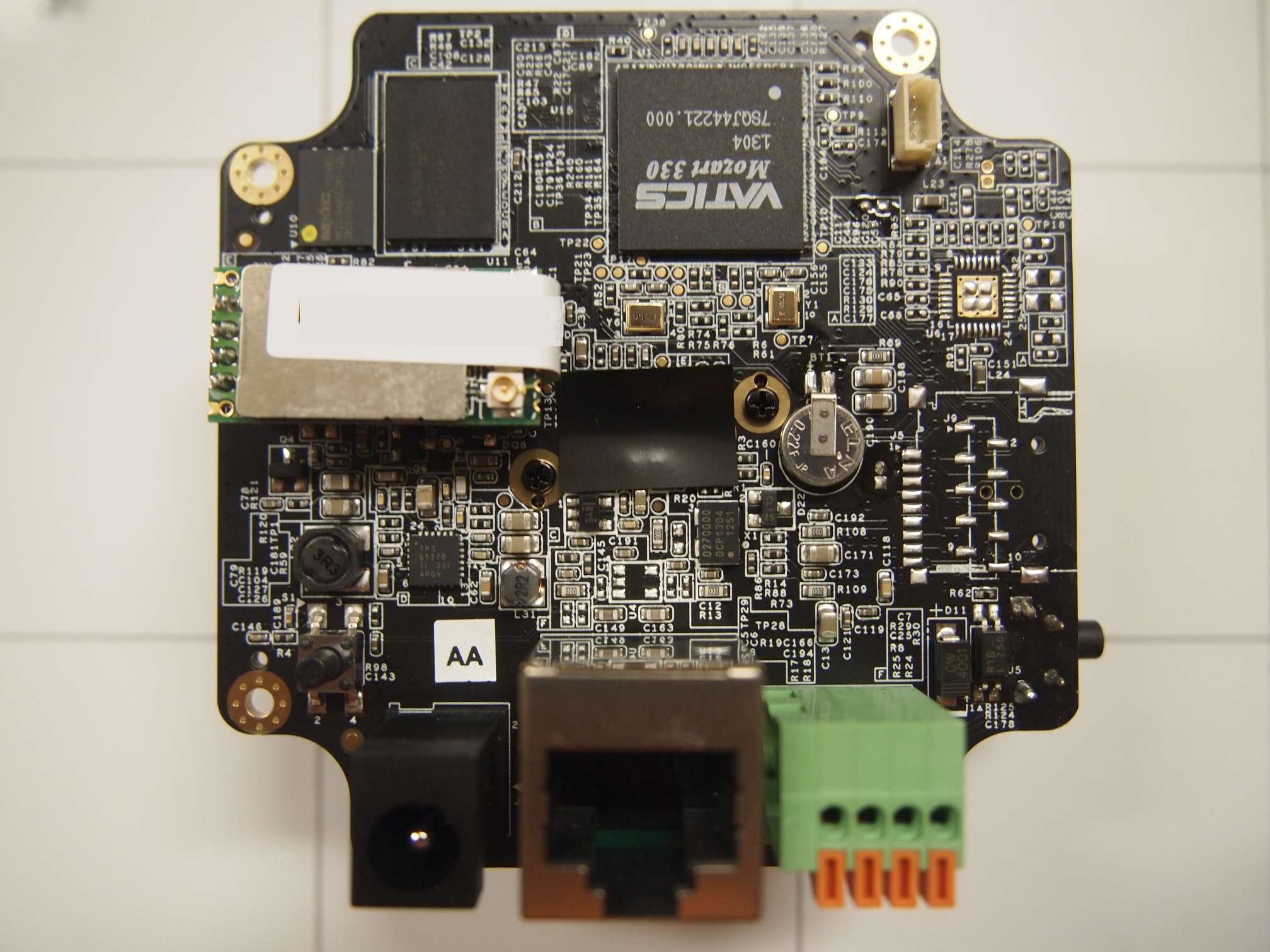
== Disassembly == | == Disassembly == | ||
<gallery> | |||
File:Alarm.com_ADC-v520IR_Front.JPG | |||
File:Alarm.com ADC-v520IR Back.JPG | |||
File:Alarm.com ADC-v520IR Back Antenna Off.JPG | |||
File:Alarm.com ADC-v520IR Cover Off.JPG | |||
File:Alarm.com ADC-v520IR IR Off.JPG | |||
File:Alarm.com ADC-v520IR IR.JPG | |||
File:Alarm.com ADC-v520IR IR Off 2.JPG | |||
File:Alarm.com ADC-v520IR Main Back.JPG | |||
File:Alarm.com ADC-v520IR Main Removed Front.JPG | |||
File:Alarm.com ADC-v520IR Main Removed Back.JPG | |||
</gallery> | |||
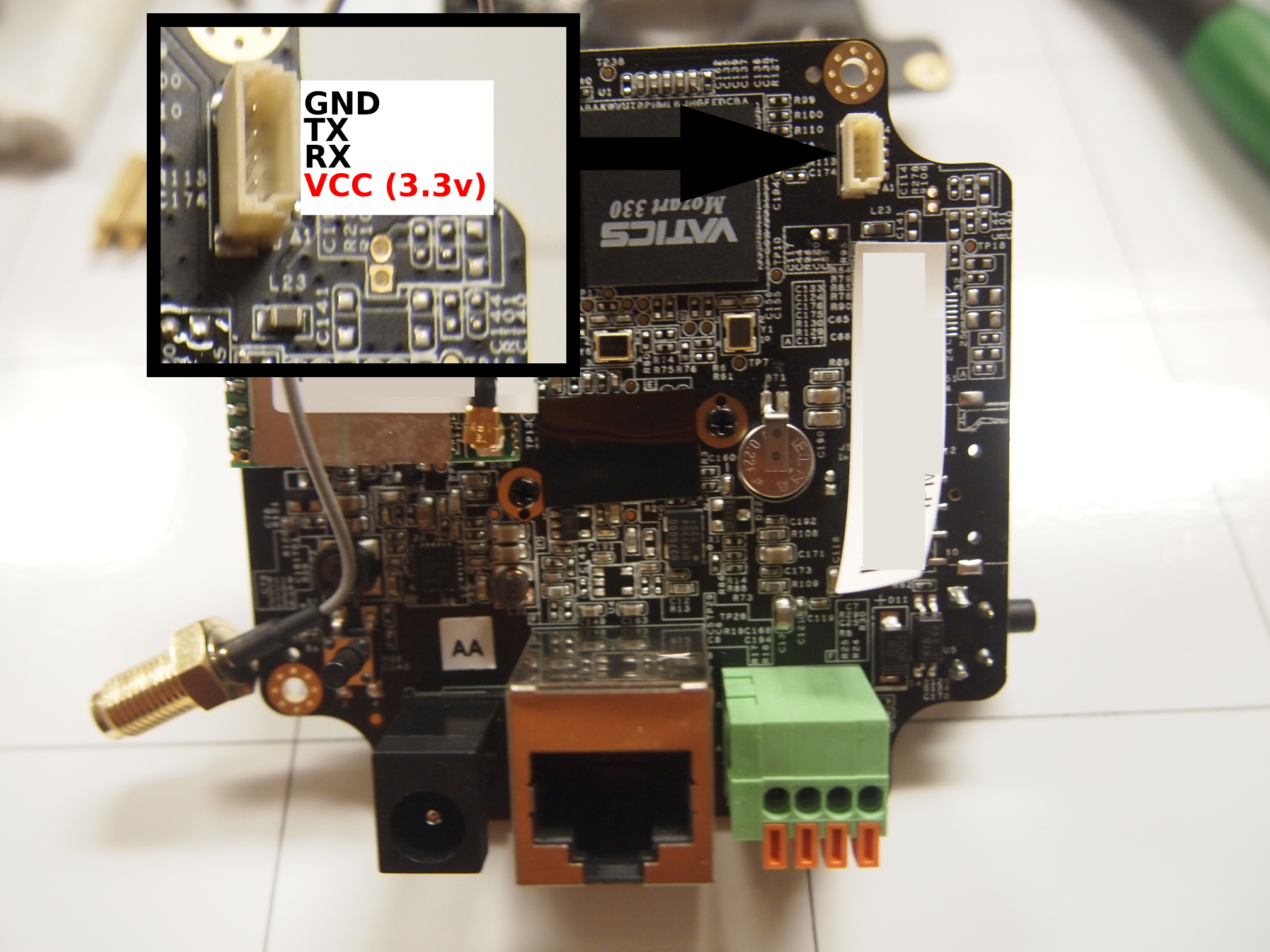
== UART == | |||
A Login Console is presented on UART (3.3v) at 38400 baud. The pinout for UART can be found below. | |||
<gallery> | |||
File:Alarm.com ADC-v520IR UART.jpg | |||
</gallery> | |||
== Exploitation == | |||
This device ships with an open U-boot installation meaning that with a UART adapter hooked up we have access to modify the default boot parameters. This opens the device to an technique called "Kernel Init Hijacking". This technique involves modifying the "init" boot argument which when passed to the kernel specifies which script will handle the boot-up process after the kernel is loaded. By defining this variable as "/bin/sh" we tell the kernel after booting to drop to a shell over UART. This allows us temporary root access to the file system. | |||
'''Kernel init Hijacking Instructions''' | |||
# Connect USB-to-TTL adapter to camera UART, pinout is available on Exploitee.rs | |||
# Press any key at correct moment (during u-boot startup) to enter u-boot shell | |||
# Modify kernel boot args: | |||
#: <pre>setenv bootargs root=/dev/mtdblock1 mem=80M console=1 rootfstype=squashfs user_debug=31 init=/bin/sh</pre> | |||
#: <pre>run bootcmd</pre> | |||
# Finish its bootup manually: | |||
#: <pre>/etc/init.d/rcS</pre> | |||
# Add a new user with: | |||
#: <pre>adduser -h /mnt/ramdisk -s /bin/sh -g "" -H username</pre> | |||
# Modify user and group to root uid/gid. (set 1000:1000 to 0:0 in passwd for new user) | |||
# Reboot! | |||
== Kernel init Hijacking Demo == | |||
{{#ev:youtube|Te8JrXF85wA}} | |||
Latest revision as of 12:05, 8 June 2015
"Although the information we release has been verified and shown to work to the best our knowledge, we cant be held accountable for bricked devices or roots gone wrong."
This page will be dedicated to a general overview, descriptions, and information related to the Alarm.com ADC-v520IR.
About
The Alarm.com ADC-v520IR is a network (Wifi/Ethernet) camera w/ IR LEDs provided by alarm.com
Disassembly
UART
A Login Console is presented on UART (3.3v) at 38400 baud. The pinout for UART can be found below.
Exploitation
This device ships with an open U-boot installation meaning that with a UART adapter hooked up we have access to modify the default boot parameters. This opens the device to an technique called "Kernel Init Hijacking". This technique involves modifying the "init" boot argument which when passed to the kernel specifies which script will handle the boot-up process after the kernel is loaded. By defining this variable as "/bin/sh" we tell the kernel after booting to drop to a shell over UART. This allows us temporary root access to the file system.
Kernel init Hijacking Instructions
- Connect USB-to-TTL adapter to camera UART, pinout is available on Exploitee.rs
- Press any key at correct moment (during u-boot startup) to enter u-boot shell
- Modify kernel boot args:
setenv bootargs root=/dev/mtdblock1 mem=80M console=1 rootfstype=squashfs user_debug=31 init=/bin/sh
run bootcmd
- Finish its bootup manually:
/etc/init.d/rcS
- Add a new user with:
adduser -h /mnt/ramdisk -s /bin/sh -g "" -H username
- Modify user and group to root uid/gid. (set 1000:1000 to 0:0 in passwd for new user)
- Reboot!