Amazon FireTV
"Although the information we release has been verified and shown to work to the best our knowledge, we cant be held accountable for bricked devices or roots gone wrong."
This page will be dedicated to a general overview, descriptions, and information related to the Amazon FireTV.
Purchase
Buying devices is expensive and, in a lot of cases our testing leads to bricked equipment. If you would like to help support our group, site, and research please use one of the links below to purchase your next device. Purchase the FireTV at Amazon
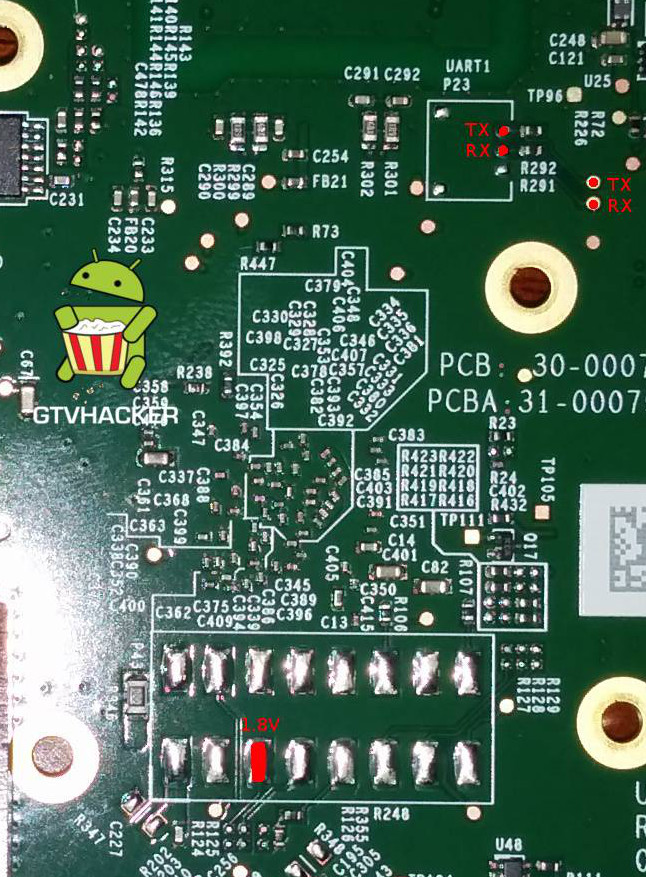
Pinouts
Exploitation
EMMC refers to an Embedded Multi-Media Card which has native Linux support. This means it works just like an SD card, and for our purposes, just filesystem access. Error Correcting Code and Out of Bounds data, which are usually a large hassle with NAND flash memory is handled in hardware, and is transparent, which makes it easier for reading and writing.
Although eMMC memory can have 9 Pins (VCC, VSS, CMD, CLK, DAT0-DAT4) it can also operate on SPI / Single Bit mode using only 1 DAT line. In short, reading/writing an eMMC chip can be done with only 5 wires, which does not require specialized hardware or software tools.
Required Minimum Connections: VCC, VSS, CMD, CLK, DAT0 (These lines all normally accessible via SMD resistors) GTVHacker recommends using a device like the SD Card Sniffer from Sparkfun to interface between your SD card reader, and the flash. By adding pins to the SD Card sniffer board, it facilitates easy analysis of the correct pinout, and also reduces the risk of damage due to repeated soldering to your SD card reader.
The Amazon FireTV utilizes an EMMC flash. Using the pinouts above, you can connect the flash to a SD card reader, and rewrite it's contents.
For the FireTV device specifically, you can mount the /system partition, which is EXT4. From here, just copy over the SuperSU APK into app, and the su binary to bin. Ensure that you properly chown the su binary (4755). This will allow for root access via ADB, and further examination of the system internals.