Difference between revisions of "Greenwave Reality Bulbs"
m (1 revision: Moving from DC22 to main site.) |
|||
| Line 38: | Line 38: | ||
The credentials originally retrieved were: <pre>root:$1$iIngN6uw$iF5XoC.xYL8sTXaWLo8yZ1:14205:0:99999:7:::</pre> | The credentials originally retrieved were: <pre>root:$1$iIngN6uw$iF5XoC.xYL8sTXaWLo8yZ1:14205:0:99999:7:::</pre> | ||
== Demo == | |||
{{#ev:youtube|bOoIETG8BFo}} | |||
Revision as of 10:45, 17 August 2014
"Although the information we release has been verified and shown to work to the best our knowledge, we cant be held accountable for bricked devices or roots gone wrong."
This page will be dedicated to a general overview, descriptions, and information related to the Greenwave Reality TCP Connected Bulbs.
Purchase
Buying devices is expensive and, in a lot of cases our testing leads to bricked equipment. If you would like to help support our group, site, and research please use one of the links below to purchase your next device. Purchase the Greenwave Reality TCP Connected Bulbs at Amazon
Disassembly
Dropbear SSHD
By default this device spawns an sshd server upon boot.
The default root credentials to the Greenwave Reality TCP Connected Smart Lighting system are:
- username:
root - password:
thinkgreen
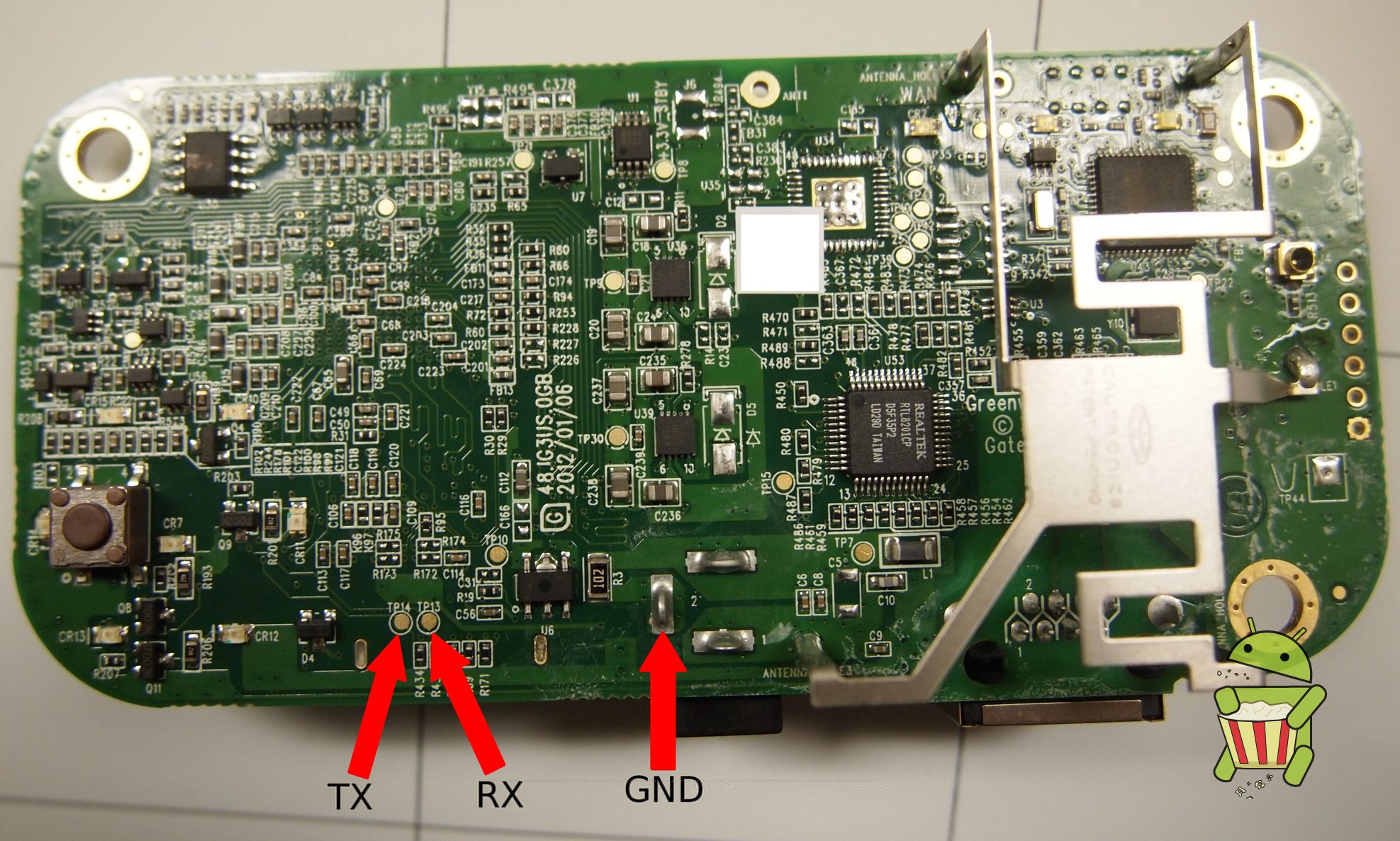
UART
The pin-out for UART can be found on the image below.
Exploitation
This device ships with an open U-boot installation meaning that with a UART adapter hooked up we have access to modify the default boot parameters. This opens the device to an technique called "Kernel Init Hijacking". This technique involves modifying the "init" boot argument which when passed to the kernel specifies which script will handle the boot-up process after the kernel is loaded. By defining this variable as "/bin/sh" we tell the kernel after booting to drop to a shell over UART. This allows us temporary root access to the file system.
With the Greenwave Reality TCP Connected Lighting System, we only had to use this mode to crack the root password. This is because by default the device runs an sshd server which allows us to login if the correct credentials are known.
The credentials originally retrieved were:
root:$1$iIngN6uw$iF5XoC.xYL8sTXaWLo8yZ1:14205:0:99999:7:::